Learn more about the coming age of identity-based payments.
Discover from the frontlines how palm vein payments have started to streamline and secure payment infrastructure. Download our white paper today to find out more.
Processing Secure Payments Via Biometric-Based Identities
Executive Summary
As the global financial landscape rapidly embraces digitization, the demand for secure, reliable, and scalable methods of identity verification and authentication has become paramount. Traditional methods such as passwords, PINs, and even more common biometrics like fingerprints are increasingly vulnerable to sophisticated fraud. Recognizing this growing need, the Saudi Central Bank (SAMA), a national entity established to develop a secure, interoperable payment infrastructure, has initiated a groundbreaking project to explore the use of palm vein biometrics. Saudi Payments, which serves both banks and FinTechs, is committed to ensuring a standardized, level playing field for financial services, while enhancing security and reducing fraud risks.
This white paper summarizes how palm vein biometrics can be integrated into a national or financial ID system and utilized as the primary modality for payment schemes and financial transactions. The purpose of the project is to demonstrate a Proof of Concept (PoC) that shows how individuals can conduct critical financial transactions, such as withdrawing and depositing money at ATMs and making payments at POS terminals, without the need for physical items like a mobile device or payment card. Instead, the unique biometric patterns within the palm of an individual’s hand will serve as their secure and highly accurate form of authentication. Palm biometric payments can replace the use of cards over time, therefore eliminating costs and vulnerabilities associated with traditional payment methods.
Fujitsu (2024) details the effectiveness of various biometrics. Unlike other biometric technologies, palm vein biometrics provide a level of security and accuracy that is unparalleled. By scanning the unique vein patterns under the skin, palm vein technology offers millions of data points. On the contrary, other biometrics, which consist of visible attributes such as fingerprints, are highly susceptible to fraud. These forms of biometrics have been exploited, leading to financial crimes such as the case detailed in 2023 (Soni) where perpetrators exploited the Aadhaar Enabled Payment System by cloning the fingerprints of their victims to perform financial transactions fraudulently. The internal nature of palm vein patterns and liveliness validation means they cannot be easily compromised or duplicated, making them the ideal biometric for high-security financial transactions.
This white paper summarizes how palm vein biometrics can be integrated into a national or financial ID system and utilized as the primary modality for payment schemes and financial transactions. The purpose of the project is to demonstrate a Proof of Concept (PoC) that shows how individuals can conduct critical financial transactions, such as withdrawing and depositing money at ATMs and making payments at POS terminals, without the need for physical items like a mobile device or payment card. Instead, the unique biometric patterns within the palm of an individual’s hand will serve as their secure and highly accurate form of authentication. Palm biometric payments can replace the use of cards over time, therefore eliminating costs and vulnerabilities associated with traditional payment methods.
Fujitsu (2024) details the effectiveness of various biometrics. Unlike other biometric technologies, palm vein biometrics provide a level of security and accuracy that is unparalleled. By scanning the unique vein patterns under the skin, palm vein technology offers millions of data points. On the contrary, other biometrics, which consist of visible attributes such as fingerprints, are highly susceptible to fraud. These forms of biometrics have been exploited, leading to financial crimes such as the case detailed in 2023 (Soni) where perpetrators exploited the Aadhaar Enabled Payment System by cloning the fingerprints of their victims to perform financial transactions fraudulently. The internal nature of palm vein patterns and liveliness validation means they cannot be easily compromised or duplicated, making them the ideal biometric for high-security financial transactions.
Understanding Palm Vein Biometric Authentication
Palm vein biometric technology is a highly advanced authentication system that uses the unique patterns of veins beneath the skin of the palm to verify an individual’s identity. By utilizing near-Infrared light, the technology captures the internal vein patterns, which are stable throughout aperson’s life and nearly impossible to replicate. These patterns are converted into a digital template for authentication, offering a secure, accurate, and scalable solution for identity verification across various industries.
Fujitsu is the pioneer of palm vein biometrics, introducing the technology for commercial use in the early 2000s. The accuracy and scalability of palm vein scanning technology can vary depending on the implementation and provider. In this project, the palm vein technology utilized is designed to meet high-security standards, providing a False Acceptance Rate (FAR) of less than 0.000001% and a False Rejection Rate (FRR) of around 0.01% (with Retry), making it an ideal choice for critical financial applications. The technology’s performance specifications are detailed further within this whitepaper.
Fujitsu is the pioneer of palm vein biometrics, introducing the technology for commercial use in the early 2000s. The accuracy and scalability of palm vein scanning technology can vary depending on the implementation and provider. In this project, the palm vein technology utilized is designed to meet high-security standards, providing a False Acceptance Rate (FAR) of less than 0.000001% and a False Rejection Rate (FRR) of around 0.01% (with Retry), making it an ideal choice for critical financial applications. The technology’s performance specifications are detailed further within this whitepaper.
Comparison To Other Biometric Modalities
.webp)
Figure 1.1: Comparison of the most common human biometric technologies by criteria of accuracy and practicability. This figure was originally published via Fujitsu (2024)
- Fingerprint: Fingerprint authentication is more commonly used but is susceptible to replication, as fingerprints can be lifted from surfaces. Palm vein technology, with a FAR of less than 0.000001%, offers a much higher level of security compared to fingerprint technology, which typically has FARs of 0.1% to 0.2%. Palm vein scanning also has a significantly lower FRR (0.01%) than fingerprint technologies, which often experience FRRs ranging from 1% to 5%.
- Facial Recognition: While facial recognition provides convenience, it can be vulnerable to spoofing with images or masks, as described in various publications such as Borak, M (2020). Facial recognition technology is also sensitive to changes in lighting or facial expressions. Facial recognition typically has FARs between 0.1% and 1%, making it less secure and impractical for identification against a large population due to the limited number of unique data points.
.webp)
Figure 1.2 False Acceptance Rate and False Rejection Rates provide a fundamental reference to theeffectiveness of human biometrics for use in practical applications and the size of the domain. This figure wasoriginally published via Fujitsu (2024)
Palm vein biometric authentication combines superior security, hygiene, and accuracy, making it a robust solution for identity verification. The technology relies on internal vein patterns that are invisible and virtually impossible to replicate, ensuring enhanced protection against fraud and identity theft. Its contactless nature not only improves hygiene, particularly in public environments like ATMs, healthcare facilities, and retail spaces, but also reduces the risk of contamination. With an exceptionally low false acceptance rate of below 0.000001% (less than one mistake in 100 million attempts) and a false rejection rate of 0.01% (with retry), it delivers high accuracy suitable for critical applications such as financial services.
Use cases
Many studies show the challenges with knowledge-based authentications (KBA) methods (i.e. methods that require the user to remember a secret string or pattern) to attacks such as shoulder surfing and impersonation (Wang, Chen, Liu). Furthermore, the user experience with passwords is poor, especially for the elderly, as they may experience difficulties with memory, making it challenging to remember complex passwords. On the contrary, financial institutions (FIs) are required to develop strong password policies for their users when accessing digital channels (e.g., length, formation, duration, aging, etc) and this creates further friction in the user experience and costs in supporting frustrated users to reset and gain access to their accounts.
Using a reliable and strong biometric authentication method, such as palm vein or facial recognition, in combination with non-KBA methods, such as device binding, offers several advantages for users, especially the elderly, eliminating the need to memorize and manage multiple passwords.
SAMA initiated this proof of concept (POC), with an emphasis on demonstrating how palm vein biometrics can be integrated into the user experience at multiple touchpoints. When the bank customer is onboarded, they can use the ATM to withdraw cash or purchase from merchants.
Saudi Arabia’s current banking and issuer/acquirer ecosystem was simulated to demonstrate these use cases where palm vein biometrics delivers improved user experience, mitigation of fraud, and high levels of security.
Using a reliable and strong biometric authentication method, such as palm vein or facial recognition, in combination with non-KBA methods, such as device binding, offers several advantages for users, especially the elderly, eliminating the need to memorize and manage multiple passwords.
SAMA initiated this proof of concept (POC), with an emphasis on demonstrating how palm vein biometrics can be integrated into the user experience at multiple touchpoints. When the bank customer is onboarded, they can use the ATM to withdraw cash or purchase from merchants.
Saudi Arabia’s current banking and issuer/acquirer ecosystem was simulated to demonstrate these use cases where palm vein biometrics delivers improved user experience, mitigation of fraud, and high levels of security.
Customer Onboarding and Palm Enrollment


Figure 2.1 The Proof of Concept project for SAMA focused on 3 personas for onboarding into the system and performing authentication. (1) An administrator to configure the solution and have oversight of activities, (2) a bank user responsible for banking customers, and (3) a customer who performs banking and payment transactions.
Financial Institutions are required to perform KYC on all individuals before doing business. Issuers (banks) will maintain their role and responsibility as issuers to perform and maintain KYC of their customers. To participate in the payment scheme, the issuer must integrate with standard APIs to onboard its customers. Issuers must provide KYC data, which is stored at the scheme and is used to generate and store biometric templates. Customers may enroll their palm vein pattern by traveling to an authorized enrollment station and securely verifying their identity via KYC data stored at the scheme. Palm enrollment devices use an encryption key to encrypt the palm vein biometric template on capture, therefore avoiding the capture and storage of raw data that could otherwise be
sensitive information. The encrypted values are then persisted in the biometric database and
referred to as a biometric template.
This use-case has been simulated as follows:
sensitive information. The encrypted values are then persisted in the biometric database and
referred to as a biometric template.
This use-case has been simulated as follows:
Account Linking
Banks issue debit and credit cards to enable customers to perform financial transactions. This project provides the ability to link a bank account directly to a person’s identity through the use of their biometrics. The person’s biometrics are then used for identification and performing financial transactions without the need for plastic cards.
To participate in the biometric-based identity payment scheme, the bank must integrate with standard APIs to perform account linking. The bank must utilize its own existing mechanisms (Such as One Time Passcode or PIN) to strongly authenticate its customers for onboarding. The bank may then assign a token to each of its customers’ accounts using a unique Issuer Identification Number (IIN) assigned to the bank by the payment scheme provider. The bank must then return the token and metadata (Account Name, Product Label, etc) to the payment scheme provider for all accounts that have been requested to be linked to the payment scheme. Once the accounts are linked, the customer may manage default accounts and preferences when performing financial transactions using their biometric identity.
To participate in the biometric-based identity payment scheme, the bank must integrate with standard APIs to perform account linking. The bank must utilize its own existing mechanisms (Such as One Time Passcode or PIN) to strongly authenticate its customers for onboarding. The bank may then assign a token to each of its customers’ accounts using a unique Issuer Identification Number (IIN) assigned to the bank by the payment scheme provider. The bank must then return the token and metadata (Account Name, Product Label, etc) to the payment scheme provider for all accounts that have been requested to be linked to the payment scheme. Once the accounts are linked, the customer may manage default accounts and preferences when performing financial transactions using their biometric identity.
Customer Identification and Transaction Processing
KYC is the foundation of customer identification. The solution links biometric templates for each individual to their KYC record. Customer identification is then supported using palm vein biometrics to uniquely identify an individual to perform authorized financial transactions.

Figure 3.1 Unique customer identification is performed by capturing the palm vein pattern within the customer’s palm. On capture, the palm vein pattern values are encrypted. The client device authenticates using a key pair to send the encrypted pattern to the matching engine. The matching engine identifies the corresponding biometric template associated with a natural person. The person’s unique identifier and tokens are returned for processing.
ATM and Banking Systems
Once a customer is onboarded and their palm vein is enrolled, their biometric template is associated with their KYC record, the customer may link any of their authorized accounts to their identity via Account Linking. Once an account is linked, the individual may scan their palm, which will identify the user and return to the issuer the authorized account token(s) to enable to customer to proceed with the financial transaction.
This capability was demonstrated with an NCR ATM as follows:
This capability was demonstrated with an NCR ATM as follows:

Figure 4.1. In place of using a debit card, the customer presents their palm, which is then captured and securely sent to the matching engine to identify the unique person. The matching engine returns the unique customer and the token(s) of authorized accounts. The customer is then presented with the ability to transact on any of the authorized accounts.
Point of Sale
Once a customer is onboarded and their palm vein is enrolled, their biometric template is associated with their KYC record. The customer may link any of their authorized accounts to their identity via Account Linking. Once an account is linked, the individual may scan their palm, which will identify the user and return to the acquirer the authorized account token(s). The transaction is routed to the correct destination for processing. The financial transaction is processed using the desired financial instrument attached to the individual’s identity. This capability was demonstrated with a point of sale terminal as follows:
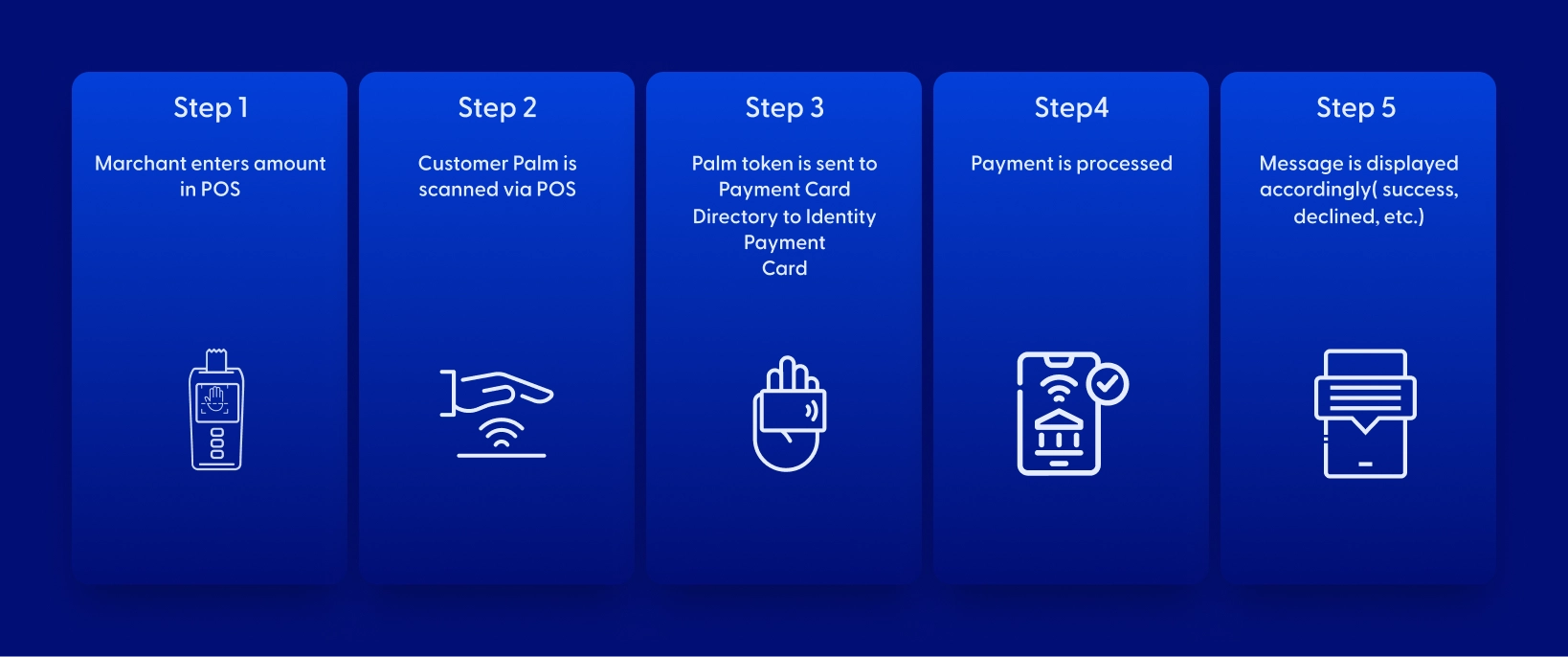
Figure 5.1. In place of using a payment card, the customer presents their palm, which is then captured and securely sent to the matching engine to identify the unique person. The matching engine returns the unique customer and the token(s) of authorized accounts. The customer is then able to pay using any authorized account.
Technical Aspects of PALM Biometric Systems
SAMA has partnered with IDCentriq to deliver the proof of concept (POC). In this POC, the Mobile POS and Standalone USB Palm Vein Sensor devices performed palm enrollment and identification services. The Standalone USB Palm Vein Sensor was directly integrated with a standard NCR ATM Machine to perform palm enrollment and identification functions. The following standard hardware devices are available from IDCentriq to facilitate palm enrollment and customer identification activities.

IDCentriq provides a platform to integrate biometrics into existing National ID systems and/or provide a Financial Digital ID (FDID). Integration with the platform is provided over a variety of channels.

Figure 6.1 IDCentriq’s platform provides identity onboarding and enrollment capabilities to populate the Identity Hub. Palm Vein-enabled devices perform identification and return FDID & linked tokens for integrated systems or processing payment transactions.
System integration and business logic, such as biometric template matching, are provided via APIs and SDKs. Physical devices such as Microsoft Windows and Linux terminals for banking systems are supported using the Standalone USB Palm Vein Scanner and supplied drivers, which communicate with the platform for business processes such as customer identification.
Support for legacy Point of Sale (POS) terminals is achieved through the Auxiliary POS Device, which connects to the legacy POS over Bluetooth. As shown in Figure 3.2, the Auxiliary POS Device performs the customer identification activity and communicates the account token to the legacy Point of Sale device to perform the standard ISO payment transaction it performs today.
Support for legacy Point of Sale (POS) terminals is achieved through the Auxiliary POS Device, which connects to the legacy POS over Bluetooth. As shown in Figure 3.2, the Auxiliary POS Device performs the customer identification activity and communicates the account token to the legacy Point of Sale device to perform the standard ISO payment transaction it performs today.

Figure 6.2 IDCentriq’s auxiliary POS device connects to existing POS terminals for minimal change and disruption to existing payment acquirers, banks, and merchants to adopt payment by identity. The same process flow is available when integrating with any other systems, such as an ATM.
Payment scheme customers can manage their Identity profile, linked accounts (including default accounts), perform step-up authentication for high-value transactions, and view transaction history through a mobile app. Biometric templates, such as palm veins, are encrypted (AES) at the time of capture and sent over encrypted channels to matching engines to process and return tokens. Tokens are passed to integrated systems to perform business processes and transactions. Biometric templates are stored as an encrypted value in an encrypted database. The encrypted biometric template does not store sensitive personal information and is not usable outside of the matching engine’s algorithm and specific key value; therefore, it provides absolute data privacy.
Future Trends and Developments
The escalating threat of security breaches across diverse industries has created a pressing need for advanced security solutions, propelling the growth of the palm vein biometrics market. As estimated by IMARC Group (2024), the global palm vein biometrics market is expected to have a compound annual growth rate exceeding 18% over the next 7 years.
Key factors driving this growth include:
Key factors driving this growth include:
- Rising adoption of biometrics for high-security applications.
- Government initiatives for unique citizen identification.
- Increasing business competition and the need for secure data protection.
- Growing utilization in financial services for secure access control, mobile banking, and customer protection.
- Widespread adoption in healthcare for patient identification, record retrieval, and enrollment.
- Deployment across government organizations to enhance security and combat unauthorized access.
Technology advancements in near-infrared light and sensors have resulted in cost reductions and improved matching algorithms to enable palm vein biometrics to be used at scale as the premier biometric for identification and authentication.
Leading solution providers add layers of encryption to nullify the benefit of stealing a palm vein biometric template, as the template is encrypted with a unique key and therefore cannot be used for any purpose.
Leading solution providers add layers of encryption to nullify the benefit of stealing a palm vein biometric template, as the template is encrypted with a unique key and therefore cannot be used for any purpose.
Additional Considerations
KSA Regulatory Framework
in the Kingdom of Saudi Arabia (KSA), the use of biometric authentication is governed by several regulatory standards and laws, as the country aims to ensure both security and privacy for users.
Personal Data and Protection Law (PDPL) by SDAIA (2023) governs how personal data, including biometric data, is collected, processed, and stored. Biometric data is considered sensitive data, which requires the data to be secured at all times and consent to be explicitly received from the individual to process the biometric data, except in cases defined by law.
PDPL requires biometric data to be stored within the borders of KSA unless specific conditions are met, such as an individual providing explicit consent after being fully informed of the purpose and scope of processing the data.
The Ministry of Interior (MOI) in Saudi Arabia enforces various regulations on biometric
identification, focusing on security, identity verification, and fraud prevention. These regulations
primarily apply to sectors such as civil affairs, immigration, border control, and law enforcement.
They address the collection, processing, and protection of biometric data, especially for foreign
nationals, citizens, and residents engaging in government services. The MOI requires biometric data to be collected from citizens as part of the national ID registration process. This data is then used for identity verification in government services and transactions.
The Saudi Central Bank (SAMA) has implemented regulations such as the Counter-Fraud Framework by SAMA (2022) that promote secure authentication methods, including biometrics, in financial services. Banks and financial institutions are required to use biometrics responsibly for identity verification while maintaining data privacy.
Communications, Space & Technology (CST) has implemented regulations to mandate the use of biometrics to verify the identity of customers in the telecommunications sector.
in the Kingdom of Saudi Arabia (KSA), the use of biometric authentication is governed by several regulatory standards and laws, as the country aims to ensure both security and privacy for users.
Personal Data and Protection Law (PDPL) by SDAIA (2023) governs how personal data, including biometric data, is collected, processed, and stored. Biometric data is considered sensitive data, which requires the data to be secured at all times and consent to be explicitly received from the individual to process the biometric data, except in cases defined by law.
PDPL requires biometric data to be stored within the borders of KSA unless specific conditions are met, such as an individual providing explicit consent after being fully informed of the purpose and scope of processing the data.
The Ministry of Interior (MOI) in Saudi Arabia enforces various regulations on biometric
identification, focusing on security, identity verification, and fraud prevention. These regulations
primarily apply to sectors such as civil affairs, immigration, border control, and law enforcement.
They address the collection, processing, and protection of biometric data, especially for foreign
nationals, citizens, and residents engaging in government services. The MOI requires biometric data to be collected from citizens as part of the national ID registration process. This data is then used for identity verification in government services and transactions.
The Saudi Central Bank (SAMA) has implemented regulations such as the Counter-Fraud Framework by SAMA (2022) that promote secure authentication methods, including biometrics, in financial services. Banks and financial institutions are required to use biometrics responsibly for identity verification while maintaining data privacy.
Communications, Space & Technology (CST) has implemented regulations to mandate the use of biometrics to verify the identity of customers in the telecommunications sector.
Interoperability of Biometrics
Interoperability across palm vein sensors can be achieved by standardizing the quality requirements of the image capturing across palm vein sensors. This approach requires a certification and governance process to maintain the security and accuracy of a platform. Interoperability protects against vendor lock-in and encourages innovation.
Interoperability of Palm Biometrics
Multiple global organizations provide standards to regulate the standards of biometric systems, including ISO/IEC (ISO/IEC 24745; ISO/IEC 30107-3; ISO/IEC 19795-1; ISO/IEC 5152:2024), ANSI, and NIST. However, palm vein biometric templates are unique to solution providers for the purpose of security and data privacy.
Interoperability across palm vein sensors can be achieved by standardizing the quality Requirements of the palm vein image capturing across palm vein sensors. This approach requires a certification and governance process to maintain the security and accuracy of a platform. Interoperability protects against vendor lock-in and encourages innovation.
During the POC, IDCentriq demonstrated the interoperability of palm vein sensors within IDCentriq's platform. While this is very important, it is equally important to ensure there are ample security controls to prevent tampering and avoid storing sensitive biometric data that can be compromised.
The platform demonstrated security controls through a secure enrollment process that converts sensitive, raw images into a mathematical array of numbers, which is then encrypted as a biometric template. The process executes within a secure enclave within the SDK and device to prevent tampering. The formula used for biometric enrollment is unique from the formula used for identification and authentication. This design prevents the need to store sensitive biometric data and significantly reduces the risk associated data leakage.
An SDK enables any compatible palm vein sensor to securely enroll and perform identification and authentication activities to authenticate the identity of individuals scanning their palm.
Interoperability across palm vein sensors can be achieved by standardizing the quality Requirements of the palm vein image capturing across palm vein sensors. This approach requires a certification and governance process to maintain the security and accuracy of a platform. Interoperability protects against vendor lock-in and encourages innovation.
During the POC, IDCentriq demonstrated the interoperability of palm vein sensors within IDCentriq's platform. While this is very important, it is equally important to ensure there are ample security controls to prevent tampering and avoid storing sensitive biometric data that can be compromised.
The platform demonstrated security controls through a secure enrollment process that converts sensitive, raw images into a mathematical array of numbers, which is then encrypted as a biometric template. The process executes within a secure enclave within the SDK and device to prevent tampering. The formula used for biometric enrollment is unique from the formula used for identification and authentication. This design prevents the need to store sensitive biometric data and significantly reduces the risk associated data leakage.
An SDK enables any compatible palm vein sensor to securely enroll and perform identification and authentication activities to authenticate the identity of individuals scanning their palm.
Conclusion
Palm vein biometric authentication is an advanced, secure, and hygienic method of identity verification that uses near-infrared light to capture the unique vein patterns beneath the skin. Its superior security is attributed to the high number of unique points of interest and internal nature of palm vein patterns, making it nearly impossible to replicate. As such, palm vein biometrics offer a significantly lower False Acceptance Rate (FAR) than fingerprint technology, which is crucial for high-security applications like financial transactions. With a low False Rejection Rate (FRR), palm vein scanning ensures high accuracy, making it suitable for sensitive environments.
As a contactless solution, it also enhances hygiene in public spaces such as ATMs and healthcare facilities, improving the user experience by eliminating the need for cards or PINs. The technology has already seen real-world applications, including in banking systems like Ogaki Kyoritsu Bank's cardless ATMs and MENA's biometric-based payment solutions. With increasing adoption in high-security sectors and government initiatives for unique citizen identification, the palm vein biometrics market is expected to grow substantially. Technological advancements continue to drive improvements in cost-effectiveness and accuracy, positioning palm vein biometrics as the leading biometric solution for secure and frictionless authentication.
In conclusion, palm vein biometric authentication represents a significant advancement in identity verification, offering a compelling combination of security, accuracy, hygiene, and user convenience. As the technology continues to evolve and its adoption expands, it is poised to play an increasingly vital role in securing our digital world.
As a contactless solution, it also enhances hygiene in public spaces such as ATMs and healthcare facilities, improving the user experience by eliminating the need for cards or PINs. The technology has already seen real-world applications, including in banking systems like Ogaki Kyoritsu Bank's cardless ATMs and MENA's biometric-based payment solutions. With increasing adoption in high-security sectors and government initiatives for unique citizen identification, the palm vein biometrics market is expected to grow substantially. Technological advancements continue to drive improvements in cost-effectiveness and accuracy, positioning palm vein biometrics as the leading biometric solution for secure and frictionless authentication.
In conclusion, palm vein biometric authentication represents a significant advancement in identity verification, offering a compelling combination of security, accuracy, hygiene, and user convenience. As the technology continues to evolve and its adoption expands, it is poised to play an increasingly vital role in securing our digital world.
References
Shinzaki, T. (2020). Use case of palm vein authentication. In Uhl, A., Busch, C., Marcel, S., & Veldhuis, R. (Eds.), Handbook of Vascular Biometrics. Advances in Computer Vision and Pattern Recognition. Springer, Cham. https://doi.org/10.1007/978-3-030-27731-4_5
Soni, Neeraj. “Aadhaar Biometric Fraud.” CyberPeace, 4 Nov. 2023, www.cyberpeace.org/resources/blogs/aadhaar-biometric-fraud.
Fujitsu. (2024). Palm Vein Pattern Authentication Technology [White paper]. Retrieved from https://www.fujitsu.com/my/imagesgig5/PalmSecure%20Whitepaper.pdf
Borak, M (2020). Companies are hacking facial recognition to make it safer. Retrieved from https://www.scmp.com/abacus/tech/article/3088834/companies-are-hacking-facial-recognition-Make-it-safer
IMARC Group (2024). Palm Vein Biometrics Market by Component, Application, and Region 2024- 2032. April 2024. IMARC Group
SDAIA (2023). Personal Data Protection Law. March 27, 2023. Retrieved from https://sdaia.gov.sa/en/SDAIA/about/Documents/Personal%20Data%20English%20V2-23April2023 %20Reviewed-.pdf
SAMA (2022). Counter Fraud Framework Saudi Central Bank. Version 1.0, October 2022. Retrieved from https://www.sama.gov.sa/en-US/RulesInstructions/CyberSecurity/Counter_Fraud_Framework.pdf
(Wang, Chen, Liu). Chen Wang, Yan Wang, Yingying Chen, Hongbo Liu, Jian Liu, User authentication on mobile devices: Approaches, threats and trends, Computer Networks Volume 170, 2020, 107118, ISSN 1389-1286, https://doi.org/10.1016/j.comnet.2020.107118 ( https://www.sciencedirect.com/science/article/pii/S1389128618312799 )
Soni, Neeraj. “Aadhaar Biometric Fraud.” CyberPeace, 4 Nov. 2023, www.cyberpeace.org/resources/blogs/aadhaar-biometric-fraud.
Fujitsu. (2024). Palm Vein Pattern Authentication Technology [White paper]. Retrieved from https://www.fujitsu.com/my/imagesgig5/PalmSecure%20Whitepaper.pdf
Borak, M (2020). Companies are hacking facial recognition to make it safer. Retrieved from https://www.scmp.com/abacus/tech/article/3088834/companies-are-hacking-facial-recognition-Make-it-safer
IMARC Group (2024). Palm Vein Biometrics Market by Component, Application, and Region 2024- 2032. April 2024. IMARC Group
SDAIA (2023). Personal Data Protection Law. March 27, 2023. Retrieved from https://sdaia.gov.sa/en/SDAIA/about/Documents/Personal%20Data%20English%20V2-23April2023 %20Reviewed-.pdf
SAMA (2022). Counter Fraud Framework Saudi Central Bank. Version 1.0, October 2022. Retrieved from https://www.sama.gov.sa/en-US/RulesInstructions/CyberSecurity/Counter_Fraud_Framework.pdf
(Wang, Chen, Liu). Chen Wang, Yan Wang, Yingying Chen, Hongbo Liu, Jian Liu, User authentication on mobile devices: Approaches, threats and trends, Computer Networks Volume 170, 2020, 107118, ISSN 1389-1286, https://doi.org/10.1016/j.comnet.2020.107118 ( https://www.sciencedirect.com/science/article/pii/S1389128618312799 )
Get in touch with us
Our team is always happy to help. Contact us now to learn more about IDCentriq and our suite of connected services.
Email:
Hello@IDCentriq.com
.svg)